
Terraformを使ってWordPress on Bitnami on AWSを新しいバージョンに移行した作業ログ(2)〜TerraformでEC2インスタンス構築〜
※「Terraformを使ってWordpress on Bitnami on AWSを新しいバージョンに移行した作業ログ」全体の目次
前回の記事はこちら
Terraformを使ってWordPress on Bitnami on AWSを新しいバージョンに移行した作業ログ(1)〜Terraformのインストール〜
今回はこの部分の作業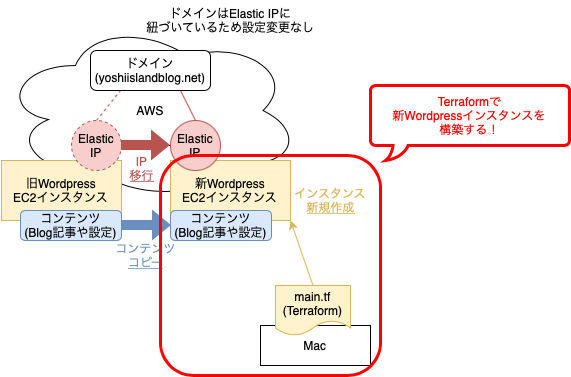
こちらのAMIを利用して構築する
※ マルチサイトの方は、後で使うAll-in-One WP Migrationでの移行が有料になってしまうので、シングルにした
参考:WordPress Multisite Certified by Bitnami and Automattic
EC2インスタンス(WordPressインスタンス)の構築
Macに作った適当な作業ディレクトリにて、「terraform init」を実行
% terraform init Initializing the backend... Initializing provider plugins... - Finding latest version of hashicorp/aws... - Installing hashicorp/aws v4.51.0... - Installed hashicorp/aws v4.51.0 (signed by HashiCorp) Terraform has created a lock file .terraform.lock.hcl to record the provider selections it made above. Include this file in your version control repository so that Terraform can guarantee to make the same selections by default when you run "terraform init" in the future. Terraform has been successfully initialized! You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, other commands will detect it and remind you to do so if necessary. %
「main.tf」というファイルを作成して、この辺りの情報を参考に、AWSに作成したい構成情報を記述していく
% vim main.tf
参考:Resource: aws_instance
参考:さくっとAWSにWordPressを立てる
最終的に作ったのは以下のようなコード
% cat main.tf
provider "aws" {
region = "ap-northeast-1" # tokyo region
}
data "aws_ami" "wordpress" {
most_recent = true
filter {
name = "name"
values = ["bitnami-wordpress-*-linux-debian-*-x86_64-hvm-ebs"]
}
}
resource "aws_security_group" "wordpress" {
name = "wordpress"
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
}
ingress {
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
}
}
resource "aws_instance" "wordpress" {
ami = data.aws_ami.wordpress.id
instance_type = "t3a.small"
key_name = "【key pair名 ※ 既存であるものを使う】" # use existing key pair
disable_api_termination = "true"
security_groups = [aws_security_group.wordpress.name]
ebs_block_device {
device_name = "/dev/xvda"
volume_size = "16" # GiB
volume_type = "gp3"
}
}
%
main.tfを書いたら「terraform validate」で文法チェック
% terraform validate Success! The configuration is valid. %
ちなみに、validateした時に出た以下のようなエラーには地道に対処した、、
% terraform validate
╷
│ Error: Unsupported argument
│
│ on main.tf line 13, in data "aws_ami" "wordpress":
│ 13: instance_type = "t3a.small"
│
│ An argument named "instance_type" is not expected here.
╵
╷
│ Error: Unsupported argument
│
│ on main.tf line 14, in data "aws_ami" "wordpress":
│ 14: key_name = "" # use existing key pair
│
│ An argument named "key_name" is not expected here.
╵
╷
│ Error: Unsupported block type
│
│ on main.tf line 16, in data "aws_ami" "wordpress":
│ 16: ebs_block_device {
│
│ Blocks of type "ebs_block_device" are not expected here.
╵
% terraform validate
╷
│ Error: Missing required argument
│
│ on main.tf line 18, in resource "aws_instance" "wordpress":
│ 18: ebs_block_device {
│
│ The argument "device_name" is required, but no definition was found.
╵
%
% terraform validate
╷
│ Error: Missing required argument
│
│ with aws_instance.wordpress,
│ on main.tf line 14, in resource "aws_instance" "wordpress":
│ 14: resource "aws_instance" "wordpress" {
│
│ "ami": one of `ami,launch_template` must be specified
╵
validateが通ったらplanコマンドで作成されるリソースを確認する
(この後叩く「apply」コマンドでも同じ結果が表示されるのでplanコマンドは必須ではない)
% terraform plan
data.aws_ami.wordpress: Reading...
data.aws_ami.wordpress: Read complete after 0s [id=【AMI ID】]
Terraform used the selected providers to generate the following execution plan.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# aws_instance.wordpress will be created
+ resource "aws_instance" "wordpress" {
+ ami = "【AMI ID】"
+ arn = (known after apply)
+ associate_public_ip_address = (known after apply)
+ availability_zone = (known after apply)
+ cpu_core_count = (known after apply)
+ cpu_threads_per_core = (known after apply)
+ disable_api_stop = (known after apply)
+ disable_api_termination = true
+ ebs_optimized = (known after apply)
+ get_password_data = false
+ host_id = (known after apply)
+ host_resource_group_arn = (known after apply)
+ iam_instance_profile = (known after apply)
+ id = (known after apply)
+ instance_initiated_shutdown_behavior = (known after apply)
+ instance_state = (known after apply)
+ instance_type = "t3a.small"
+ ipv6_address_count = (known after apply)
+ ipv6_addresses = (known after apply)
+ key_name = "【key name】"
+ monitoring = (known after apply)
+ outpost_arn = (known after apply)
+ password_data = (known after apply)
+ placement_group = (known after apply)
+ placement_partition_number = (known after apply)
+ primary_network_interface_id = (known after apply)
+ private_dns = (known after apply)
+ private_ip = (known after apply)
+ public_dns = (known after apply)
+ public_ip = (known after apply)
+ secondary_private_ips = (known after apply)
+ security_groups = [
+ "wordpress",
]
+ source_dest_check = true
+ subnet_id = (known after apply)
+ tags_all = (known after apply)
+ tenancy = (known after apply)
+ user_data = (known after apply)
+ user_data_base64 = (known after apply)
+ user_data_replace_on_change = false
+ vpc_security_group_ids = (known after apply)
+ capacity_reservation_specification {
+ capacity_reservation_preference = (known after apply)
+ capacity_reservation_target {
+ capacity_reservation_id = (known after apply)
+ capacity_reservation_resource_group_arn = (known after apply)
}
}
+ ebs_block_device {
+ delete_on_termination = true
+ device_name = "/dev/xvda"
+ encrypted = (known after apply)
+ iops = (known after apply)
+ kms_key_id = (known after apply)
+ snapshot_id = (known after apply)
+ throughput = (known after apply)
+ volume_id = (known after apply)
+ volume_size = 16
+ volume_type = "gp3"
}
+ enclave_options {
+ enabled = (known after apply)
}
+ ephemeral_block_device {
+ device_name = (known after apply)
+ no_device = (known after apply)
+ virtual_name = (known after apply)
}
+ maintenance_options {
+ auto_recovery = (known after apply)
}
+ metadata_options {
+ http_endpoint = (known after apply)
+ http_put_response_hop_limit = (known after apply)
+ http_tokens = (known after apply)
+ instance_metadata_tags = (known after apply)
}
+ network_interface {
+ delete_on_termination = (known after apply)
+ device_index = (known after apply)
+ network_card_index = (known after apply)
+ network_interface_id = (known after apply)
}
+ private_dns_name_options {
+ enable_resource_name_dns_a_record = (known after apply)
+ enable_resource_name_dns_aaaa_record = (known after apply)
+ hostname_type = (known after apply)
}
+ root_block_device {
+ delete_on_termination = (known after apply)
+ device_name = (known after apply)
+ encrypted = (known after apply)
+ iops = (known after apply)
+ kms_key_id = (known after apply)
+ tags = (known after apply)
+ throughput = (known after apply)
+ volume_id = (known after apply)
+ volume_size = (known after apply)
+ volume_type = (known after apply)
}
}
# aws_security_group.wordpress will be created
+ resource "aws_security_group" "wordpress" {
+ arn = (known after apply)
+ description = "Managed by Terraform"
+ egress = [
+ {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ description = ""
+ from_port = 0
+ ipv6_cidr_blocks = [
+ "::/0",
]
+ prefix_list_ids = []
+ protocol = "-1"
+ security_groups = []
+ self = false
+ to_port = 0
},
]
+ id = (known after apply)
+ ingress = [
+ {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ description = ""
+ from_port = 443
+ ipv6_cidr_blocks = [
+ "::/0",
]
+ prefix_list_ids = []
+ protocol = "tcp"
+ security_groups = []
+ self = false
+ to_port = 443
},
+ {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ description = ""
+ from_port = 80
+ ipv6_cidr_blocks = [
+ "::/0",
]
+ prefix_list_ids = []
+ protocol = "tcp"
+ security_groups = []
+ self = false
+ to_port = 80
},
]
+ name = "wordpress"
+ name_prefix = (known after apply)
+ owner_id = (known after apply)
+ revoke_rules_on_delete = false
+ tags_all = (known after apply)
+ vpc_id = (known after apply)
}
Plan: 2 to add, 0 to change, 0 to destroy.
───────────────────────────────────────────────────────────────────────────────────
%
問題なければ「apply」コマンドで実際にAWSリソースを作成する
(「Do you want to perform these actions?」と聞かれたらyesと入力してenter)
% terraform apply
data.aws_ami.wordpress: Reading...
data.aws_ami.wordpress: Read complete after 0s [id=【AMI ID】]
Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following
symbols:
+ create
Terraform will perform the following actions:
# aws_instance.wordpress will be created
+ resource "aws_instance" "wordpress" {
+ ami = "【AMI ID】"
+ arn = (known after apply)
+ associate_public_ip_address = (known after apply)
+ availability_zone = (known after apply)
+ cpu_core_count = (known after apply)
+ cpu_threads_per_core = (known after apply)
+ disable_api_stop = (known after apply)
+ disable_api_termination = true
+ ebs_optimized = (known after apply)
+ get_password_data = false
+ host_id = (known after apply)
+ host_resource_group_arn = (known after apply)
+ iam_instance_profile = (known after apply)
+ id = (known after apply)
+ instance_initiated_shutdown_behavior = (known after apply)
+ instance_state = (known after apply)
+ instance_type = "t3a.small"
+ ipv6_address_count = (known after apply)
+ ipv6_addresses = (known after apply)
+ key_name = "【key name】"
+ monitoring = (known after apply)
+ outpost_arn = (known after apply)
+ password_data = (known after apply)
+ placement_group = (known after apply)
+ placement_partition_number = (known after apply)
+ primary_network_interface_id = (known after apply)
+ private_dns = (known after apply)
+ private_ip = (known after apply)
+ public_dns = (known after apply)
+ public_ip = (known after apply)
+ secondary_private_ips = (known after apply)
+ security_groups = [
+ "wordpress",
]
+ source_dest_check = true
+ subnet_id = (known after apply)
+ tags_all = (known after apply)
+ tenancy = (known after apply)
+ user_data = (known after apply)
+ user_data_base64 = (known after apply)
+ user_data_replace_on_change = false
+ vpc_security_group_ids = (known after apply)
+ capacity_reservation_specification {
+ capacity_reservation_preference = (known after apply)
+ capacity_reservation_target {
+ capacity_reservation_id = (known after apply)
+ capacity_reservation_resource_group_arn = (known after apply)
}
}
+ ebs_block_device {
+ delete_on_termination = true
+ device_name = "/dev/xvda"
+ encrypted = (known after apply)
+ iops = (known after apply)
+ kms_key_id = (known after apply)
+ snapshot_id = (known after apply)
+ throughput = (known after apply)
+ volume_id = (known after apply)
+ volume_size = 16
+ volume_type = "gp3"
}
+ enclave_options {
+ enabled = (known after apply)
}
+ ephemeral_block_device {
+ device_name = (known after apply)
+ no_device = (known after apply)
+ virtual_name = (known after apply)
}
+ maintenance_options {
+ auto_recovery = (known after apply)
}
+ metadata_options {
+ http_endpoint = (known after apply)
+ http_put_response_hop_limit = (known after apply)
+ http_tokens = (known after apply)
+ instance_metadata_tags = (known after apply)
}
+ network_interface {
+ delete_on_termination = (known after apply)
+ device_index = (known after apply)
+ network_card_index = (known after apply)
+ network_interface_id = (known after apply)
}
+ private_dns_name_options {
+ enable_resource_name_dns_a_record = (known after apply)
+ enable_resource_name_dns_aaaa_record = (known after apply)
+ hostname_type = (known after apply)
}
+ root_block_device {
+ delete_on_termination = (known after apply)
+ device_name = (known after apply)
+ encrypted = (known after apply)
+ iops = (known after apply)
+ kms_key_id = (known after apply)
+ tags = (known after apply)
+ throughput = (known after apply)
+ volume_id = (known after apply)
+ volume_size = (known after apply)
+ volume_type = (known after apply)
}
}
# aws_security_group.wordpress will be created
+ resource "aws_security_group" "wordpress" {
+ arn = (known after apply)
+ description = "Managed by Terraform"
+ egress = [
+ {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ description = ""
+ from_port = 0
+ ipv6_cidr_blocks = [
+ "::/0",
]
+ prefix_list_ids = []
+ protocol = "-1"
+ security_groups = []
+ self = false
+ to_port = 0
},
]
+ id = (known after apply)
+ ingress = [
+ {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ description = ""
+ from_port = 443
+ ipv6_cidr_blocks = [
+ "::/0",
]
+ prefix_list_ids = []
+ protocol = "tcp"
+ security_groups = []
+ self = false
+ to_port = 443
},
+ {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ description = ""
+ from_port = 80
+ ipv6_cidr_blocks = [
+ "::/0",
]
+ prefix_list_ids = []
+ protocol = "tcp"
+ security_groups = []
+ self = false
+ to_port = 80
},
]
+ name = "wordpress"
+ name_prefix = (known after apply)
+ owner_id = (known after apply)
+ revoke_rules_on_delete = false
+ tags_all = (known after apply)
+ vpc_id = (known after apply)
}
Plan: 2 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
aws_security_group.wordpress: Creating...
aws_security_group.wordpress: Creation complete after 3s [id=【Security group ID】]
aws_instance.wordpress: Creating...
aws_instance.wordpress: Still creating... [10s elapsed]
aws_instance.wordpress: Creation complete after 13s [id=【Instance ID】]
Apply complete! Resources: 2 added, 0 changed, 0 destroyed.
%
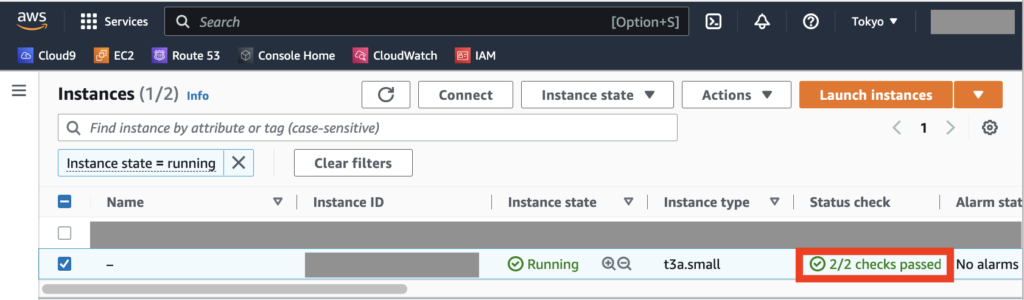
AWSマネジメントコンソールで確認すると、新しいインスタンスが作られて
「Status check」が「Initializing」からしばらく(〜数分)すると「Status check」が「2/2 checks passed」となる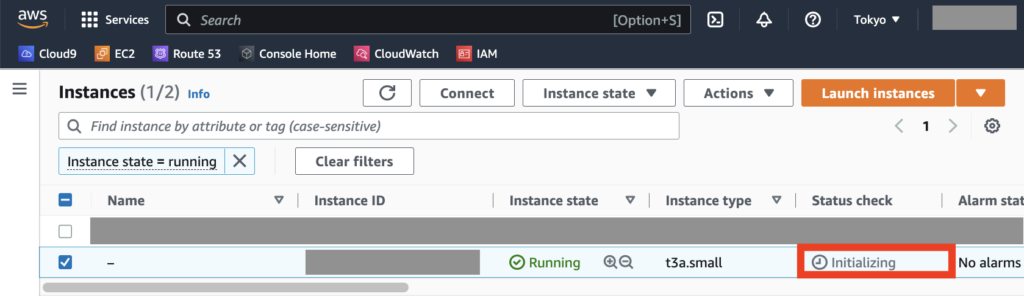
次回へ続く
Terraformを使ってWordPress on Bitnami on AWSを新しいバージョンに移行した作業ログ(3)〜WordPressログイン〜





